SIEM Download overview
Using the Elastic free SIEM technology is great to protect your applications and your company against any kind of cybercrime. You can detect, investigate and respond to any evolving threats. Its a useful foundation for every Security operations centre (SOC). The following downloads offering powerful extensions to the Elastic free SIEM technology.
SIEM examples
More about SIEM
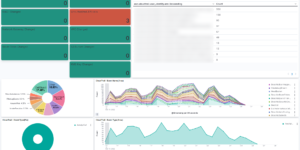
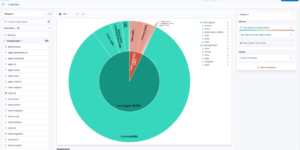
The heart of Elastic SIEM is the an interactive Kibana app. That workspace allowing teams to detect anomalous behaviour, to sort out events and start investigations. Using the Elastic agent the user has limitless possibilities to ingest from OOTB integrations.
In combination with Elastic Machine Learning you have everything in place you need to protect your company. Improve your threat detection capabilities by using threat intelligence in combination with other security rules.
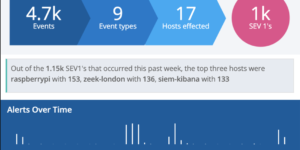
Continuously protect your environment using behaviour-based rules that detect potential risks through behaviours and tools. Analyse and prioritize potential threats based on enemy behaviour. With risk and severity scores, you can go right to the point. Detections are linked with MITRE ATT&CK®, are updated on a regular basis, and are openly provided for instant use.