Elastic Security Download overview
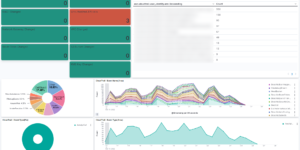
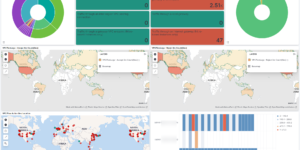
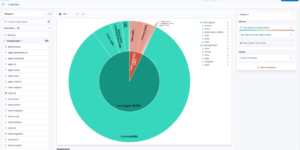
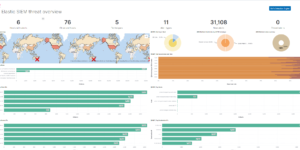
Elastic Security is the combination of SIEM and Endpoint protection within one single tool. While the Elastic Security Endpoint agent is collecting data from the host for the SIEM it also actively prevents against Malware and Ransomware attacks. Since v. 7.14 Elastic has the first open and limitless XDR solution in the market. Users of the free ELK stack based SIEM solution get the ability to prevent, detect, and respond to threats before adversaries can steal sensitive information or sabotage operations. The Kibana dashboards in this category helping to get better overview about security related data within in the Elastic Stack. They also show how to use the results of the SIEM detection engine to get better understanding of the current system status. In addition to that you also find additional alerting rules in this section.
Elastic Security downloads
More about Elastic Security
Elastic Security unites two critical components of cybersecurity — endpoint security and SIEM — to prevent, detect, and respond to threats. Building blocks for the industries first open and limitless XDR solution.
Elastic Security helps you
- Automate threat detection to identify priority issues before damage occurs
- Leverage machine learning to improve accuracy at scale
- Customize workflows and visualizations to accelerate investigations and response
- Collaborate with case management and third-party integrations to increase team efficiency