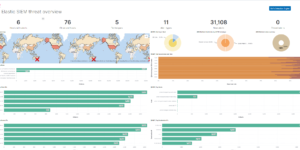
Detection rules Download overview
Detection rules downloads
More about Detection rules
The SIEM detection rules for Elastic Security defining how the Elastic Security detection engine is investigating for threats. The detection rules are a common set of rules that can be used to analyze existing data. Elastic delivers many rules OOTB. Show all pre build Elastic rules.
By using the defined fields and categories in ECS (Elastic Common Schema), rules automatically work with Beats logs, Elastic agent data and other data sources that map properly to ECS.
Elastic has opened the repository for this rules to let the community contribute to the rules. However there are other projects like Sigma that producing SIEM detection rules for different systems.