Sigma Sysmon detection rules
A collection of rules based on the Sigma detection rules for Windows Sysmon events based on Winlogbeat data.
Sigma Windows inbuilt detection rules
A collection of rules based on the Sigma rules for Windows (inbuilt folder) based on Winlogbeat data .
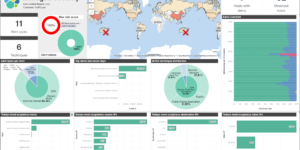
Detection engine alerts overview dashboard
Average rating:
Kibana Canvas dashboard that shows an aggregated view on the results of the detection engine in Elastic Security.
Sigma Windows Process Creation detection rules
A collection of rules based on the Sigma rules for Windows (process creation folder) based on Winlogbeat data .
Sigma detection rules for proxy server logs
A collection of rules based on the Sigma detection rules for proxy server and web server looks, e.g. zeek or suricata.
The search results are evaluated by ElasticPress using Elasticsearch clusters from Elastic Cloud.