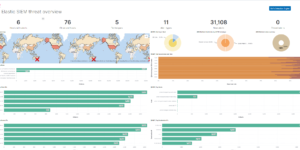
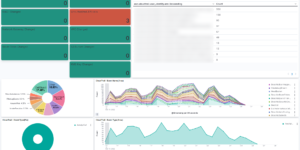
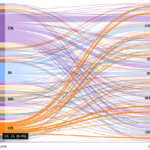
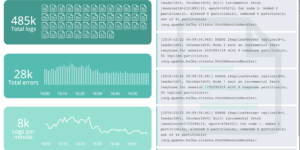
Description
This is a collection of SIEM detection rules in Elastic Security for Windows based on the Sigma project. This rule collection checks about process creation threats.
SIEM detection rules
CMSTP Execution Process Creation
Detects various indicators of Microsoft Connection Manager Profile Installer execution
DNS Tunnel Technique from MuddyWater
Detecting DNS tunnel activity for Muddywater actor
Windows Credential Editor
Detects the use of Windows Credential Editor (WCE)
Logon Scripts (UserInitMprLogonScript)
Detects creation or execution of UserInitMprLogonScript persistence method
Suspicious Plink Remote Forwarding
Detects suspicious Plink tunnel remote forarding to a local port
Advanced IP Scanner
Detects the use of Advanced IP Scanner. Seems to be a popular tool for ransomware groups.
AdFind Usage Detection
AdFind continues to be seen across majority of breaches. It is used to domain trust discovery to plan out subsequent steps in the attack chain.
APT29
This method detects a suspicious powershell command line combination as used by APT29 in a campaign against US think tanks
Baby Shark Activity
Detects activity that could be related to Baby Shark malware
Judgement Panda Credential Access Activity
Detects Russian group activity as described in Global Threat Report 2019 by Crowdstrike
BlueMashroom DLL Load
Detects a suspicious DLL loading from AppData Local path as described in BlueMashroom report
WMIExec VBS Script
Detects suspicious file execution by wscript and cscript
CrackMapExecWin
Detects CrackMapExecWin Activity as Described by NCSC
Elise Backdoor
Detects Elise backdoor acitivty as used by APT32
Emissary Panda Malware SLLauncher
Detects the execution of DLL side-loading malware used by threat group Emissary Panda aka APT27
Equation Group DLL_U Load
Detects a specific tool and export used by EquationGroup
EvilNum Golden Chickens Deployment via OCX Files
Detects Golden Chickens deployment method as used by Evilnum in report published in July 2020
Greenbug Campaign Indicators
Detects tools and process executions as observed in a Greenbug campaign in May 2020
Exchange Exploitation Activity
Detects activity observed by different researchers to be HAFNIUM group acitivity (or related) on Exchange servers
Hurricane Panda Activity
Detects Hurricane Panda Activity
Judgement Panda Exfil Activity
Detects Judgement Panda activity as described in Global Threat Report 2019 by Crowdstrike
Ke3chang Registry Key Modifications
Detects Registry modifications performed by Ke3chang malware in campaigns running in 2019 and 2020
Lazarus Activity
Detects different process creation events as described in various threat reports on Lazarus group activity
Lazarus Loaders
Detects different loaders as described in various threat reports on Lazarus group activity
Lazarus Session Highjacker
Detects executables launched outside their default directories as used by Lazarus Group (Bluenoroff)
Mustang Panda Dropper
Detects specific process parameters as used by Mustang Panda droppers
Sofacy Trojan Loader Activity
Detects Trojan loader acitivty as used by APT28
Ps.exe Renamed SysInternals Tool
Detects renamed SysInternals tool execution with a binary named ps.exe as used by Dragonfly APT group and documented in TA17-293A report
TA505 Dropper Load Pattern
Detects mshta loaded by wmiprvse as parent as used by TA505 malicious documents
TAIDOOR RAT DLL Load
Detects specific process characteristics of Chinese TAIDOOR RAT malware load
TropicTrooper Campaign November 2018
Detects TropicTrooper activity, an actor who targeted high-profile organizations in the energy and food and beverage sectors in Asia
Turla Group Commands May 2020
Detects commands used by Turla group as reported by ESET in May 2020
UNC2452 Process Creation Patterns
Detects a specific process creation patterns as seen used by UNC2452 and provided by Microsoft as Microsoft Defender ATP queries
UNC2452 PowerShell Pattern
Detects a specific PowerShell command line pattern used by the UNC2452 actors as mentioned in Microsoft and Symantec reports
Winnti Malware HK University Campaign
Detects specific process characteristics of Winnti malware noticed in Dec/Jan 2020 in a campaign against Honk Kong universities
Winnti Pipemon Characteristics
Detects specific process characteristics of Winnti Pipemon malware reported by ESET
ZxShell Malware
Detects a ZxShell start by the called and well-known function name
Hiding Files with Attrib.exe
Detects usage of attrib.exe to hide files from users.
Modification of Boot Configuration
Identifies use of the bcdedit command to delete boot configuration data. This tactic is sometimes used as by malware or an attacker as a destructive technique.
SquiblyTwo
Detects WMI SquiblyTwo Attack with possible renamed WMI by looking for imphash
Change Default File Association
When a file is opened, the default program used to open the file (also called the file association or handler) is checked. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Applications can modify the file association for a given file extension to call an arbitrary program when a file with the given extension is opened.
Cmdkey Cached Credentials Recon
Detects usage of cmdkey to look for cached credentials
CMSTP UAC Bypass via COM Object Access
Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects
Cmd.exe CommandLine Path Traversal
detects the usage of path traversal in cmd.exe indicating possible command/argument confusion/hijacking
Control Panel Items
Detects the malicious use of a control panel item
Copying Sensitive Files with Credential Data
Files with well-known filenames (sensitive files with credential data) copying
Fireball Archer Install
Detects Archer malware invocation via rundll32
Maze Ransomware
Detects specific process characteristics of Maze ransomware word document droppers
Snatch Ransomware
Detects specific process characteristics of Snatch ransomware word document droppers
Data Compressed – rar.exe
An adversary may compress data (e.g., sensitive documents) that is collected prior to exfiltration in order to make it portable and minimize the amount of data sent over the network
DNS Exfiltration and Tunneling Tools Execution
Well-known DNS Exfiltration tools execution
Domain Trust Discovery
Detects a discovery of domain trusts
Encoded FromBase64String
Detects a base64 encoded FromBase64String keyword in a process command line
Encoded IEX
Detects a base64 encoded IEX command string in a process command line
COMPlus_ETWEnabled Command Line Arguments
Potential adversaries stopping ETW providers recording loaded .NET assemblies.
Exfiltration and Tunneling Tools Execution
Execution of well known tools for data exfiltration and tunneling
Exploit for CVE-2015-1641
Detects Winword starting uncommon sub process MicroScMgmt.exe as used in exploits for CVE-2015-1641
Exploit for CVE-2017-0261
Detects Winword starting uncommon sub process FLTLDR.exe as used in exploits for CVE-2017-0261 and CVE-2017-0262
Droppers Exploiting CVE-2017-11882
Detects exploits that use CVE-2017-11882 to start EQNEDT32.EXE and other sub processes like mshta.exe
Exploit for CVE-2017-8759
Detects Winword starting uncommon sub process csc.exe as used in exploits for CVE-2017-8759
Exploiting SetupComplete.cmd CVE-2019-1378
Detects exploitation attempt of privilege escalation vulnerability via SetupComplete.cmd and PartnerSetupComplete.cmd described in CVE-2019-1378
Exploiting CVE-2019-1388
Detects an exploitation attempt in which the UAC consent dialogue is used to invoke an Internet Explorer process running as LOCAL_SYSTEM
Exploited CVE-2020-10189 Zoho ManageEngine
Detects the exploitation of Zoho ManageEngine Desktop Central Java Deserialization vulnerability reported as CVE-2020-10189
Suspicious PrinterPorts Creation (CVE-2020-1048)
Detects new commands that add new printer port which point to suspicious file
DNS RCE CVE-2020-1350
Detects exploitation of DNS RCE bug reported in CVE-2020-1350 by the detection of suspicious sub process
File or Folder Permissions Modifications
Detects a file or folder permissions modifications
Grabbing Sensitive Hives via Reg Utility
Dump sam, system or security hives using REG.exe utility
Bloodhound and Sharphound Hack Tool
Detects command line parameters used by Bloodhound and Sharphound hack tools
Koadic Execution
Detects command line parameters used by Koadic hack tool
Rubeus Hack Tool
Detects command line parameters used by Rubeus hack tool
SecurityXploded Tool
Detects the execution of SecurityXploded Tools
HH.exe Execution
Identifies usage of hh.exe executing recently modified .chm files.
HTML Help Shell Spawn
Detects a suspicious child process of a Microsoft HTML Help system when executing compiled HTML files (.chm)
Suspicious HWP Sub Processes
Detects suspicious Hangul Word Processor (Hanword) sub processes that could indicate an exploitation
Impacket Lateralization Detection
Detects wmiexec/dcomexec/atexec/smbexec from Impacket framework
Indirect Command Execution
Detect indirect command execution via Program Compatibility Assistant pcalua.exe or forfiles.exe
Suspicious Debugger Registration Cmdline
Detects the registration of a debugger for a program that is available in the logon screen (sticky key backdoor).
Interactive AT Job
Detect an interactive AT job, which may be used as a form of privilege escalation
Windows Kernel and 3rd-Party Drivers Exploits Token Stealing
Detection of child processes spawned with SYSTEM privileges by parents with non-SYSTEM privileges and Medium integrity level
MSHTA Spwaned by SVCHOST
Detects MSHTA.EXE spwaned by SVCHOST as seen in LethalHTA and described in report
Local Accounts Discovery
Local accounts, System Owner/User discovery using operating systems utilities
LSASS Memory Dumping
Detect creation of dump files containing the memory space of lsass.exe, which contains sensitive credentials. Identifies usage of Sysinternals procdump.exe to export the memory space of lsass.exe which contains sensitive credentials.
Dridex Process Pattern
Detects typical Dridex process patterns
DTRACK Process Creation
Detects specific process parameters as seen in DTRACK infections
Emotet Process Creation
Detects all Emotet like process executions that are not covered by the more generic rules
Formbook Process Creation
Detects Formbook like process executions that inject code into a set of files in the System32 folder, which executes a special command command line to delete the dropper from the AppData Temp folder. We avoid false positives by excluding all parent process with command line parameters.
NotPetya Ransomware Activity
Detects NotPetya ransomware activity in which the extracted passwords are passed back to the main module via named pipe, the file system journal of drive C is deleted and windows eventlogs are cleared using wevtutil
QBot Process Creation
Detects QBot like process executions
Ryuk Ransomware
Detects Ryuk ransomware activity
WScript or CScript Dropper
Detects wscript/cscript executions of scripts located in user directories
Trickbot Malware Recon Activity
Trickbot enumerates domain/network topology and executes certain commands automatically every few minutes. This detectors attempts to identify that activity based off a command rarely observed in an enterprise network.
Trickbot Malware Activity
Detects Trickbot malware process tree pattern in which rundll32.exe is parent of wermgr.exe
WannaCry Ransomware
Detects WannaCry ransomware activity
MavInject Process Injection
Detects process injection using the signed Windows tool Mavinject32.exe
Meterpreter or Cobalt Strike Getsystem Service Start
Detects the use of getsystem Meterpreter/Cobalt Strike command by detecting a specific service starting
Mimikatz Command Line
Detection well-known mimikatz command line arguments
MMC Spawning Windows Shell
Detects a Windows command line executable started from MMC
Mshta JavaScript Execution
Identifies suspicious mshta.exe commands
MSHTA Spawning Windows Shell
Detects a Windows command line executable started from MSHTA
Netsh RDP Port Opening
Detects netsh commands that opens the port 3389 used for RDP, used in Sarwent Malware
Netsh Port or Application Allowed
Allow Incoming Connections by Port or Application on Windows Firewall
Netsh Program Allowed with Suspcious Location
Detects Netsh commands that allows a suspcious application location on Windows Firewall
Capture a Network Trace with netsh.exe
Detects capture a network trace via netsh.exe trace functionality
Netsh Port Forwarding
Detects netsh commands that configure a port forwarding
Netsh RDP Port Forwarding
Detects netsh commands that configure a port forwarding of port 3389 used for RDP
Harvesting of Wifi Credentials Using netsh.exe
Detect the harvesting of wifi credentials using netsh.exe
Network Sniffing
Network sniffing refers to using the network interface on a system to monitor or capture information sent over a wired or wireless connection. An adversary may place a network interface into promiscuous mode to passively access data in transit over the network, or use span ports to capture a larger amount of data.
Windows Network Enumeration
Identifies attempts to enumerate hosts in a network using the built-in Windows net.exe tool.
Net.exe User Account Creation
Identifies creation of local users via the net.exe command
New Service Creation
Detects creation of a new service
Non Interactive PowerShell
Detects non-interactive PowerShell activity by looking at powershell.exe with not explorer.exe as a parent.
Microsoft Office Product Spawning Windows Shell
Detects a Windows command and scripting interpreter executable started from Microsoft Word, Excel, Powerpoint, Publisher and Visio
MS Office Product Spawning Exe in User Dir
Detects an executable in the users directory started from Microsoft Word, Excel, Powerpoint, Publisher or Visio
Executable Used by PlugX in Uncommon Location
Detects the execution of an executable that is typically used by PlugX for DLL side loading started from an uncommon location
Possible Applocker Bypass
Detects execution of executables that can be used to bypass Applocker whitelisting
Detection of Possible Rotten Potato
Detection of child processes spawned with SYSTEM privileges by parents with LOCAL SERVICE or NETWORK SERVICE privileges
Powershell AMSI Bypass via .NET Reflection
Detects Request to amsiInitFailed that can be used to disable AMSI Scanning
Audio Capture via PowerShell
Detects audio capture via PowerShell Cmdlet
PowerShell Base64 Encoded Shellcode
Detects Base64 encoded Shellcode
Suspicious Bitsadmin Job via PowerShell
Detect download by BITS jobs via PowerShell
Detection of PowerShell Execution via DLL
Detects PowerShell Strings applied to rundll as seen in PowerShdll.dll
PowerShell Downgrade Attack
Detects PowerShell downgrade attack by comparing the host versions with the actually used engine version 2.0
PowerShell Download from URL
Detects a Powershell process that contains download commands in its command line string
FromBase64String Command Line
Detects suspicious FromBase64String expressions in command line arguments
Powershell Reverse Shell Connection
Detects the Nishang Invoke-PowerShellTcpOneLine reverse shell
Suspicious PowerShell Parameter Substring
Detects suspicious PowerShell invocation with a parameter substring
Suspicious XOR Encoded PowerShell Command Line
Detects suspicious powershell process which includes bxor command, alternative obfuscation method to b64 encoded commands.
Bitsadmin Download
Detects usage of bitsadmin downloading a file
Process Dump via Rundll32 and Comsvcs.dll
Detects a process memory dump performed via ordinal function 24 in comsvcs.dll
Windows Processes Suspicious Parent Directory
Detect suspicious parent processes of well-known Windows processes
PsExec Service Start
Detects a PsExec service start
Query Registry
Adversaries may interact with the Windows Registry to gather information about the system, configuration, and installed software.
MSTSC Shadowing
Detects RDP session hijacking by using MSTSC shadowing
RedMimicry Winnti Playbook Execute
Detects actions caused by the RedMimicry Winnti playbook
Remote PowerShell Session
Detects remote PowerShell sections by monitoring for wsmprovhost as a parent or child process (sign of an active ps remote session)
Discovery of a System Time
Identifies use of various commands to query a systems time. This technique may be used before executing a scheduled task or to discover the time zone of a target system.
Renamed Binary
Detects the execution of a renamed binary often used by attackers or malware leveraging new Sysmon OriginalFileName datapoint.
Highly Relevant Renamed Binary
Detects the execution of a renamed binary often used by attackers or malware leveraging new Sysmon OriginalFileName datapoint.
Renamed jusched.exe
Detects renamed jusched.exe used by cobalt group
Execution of Renamed PaExec
Detects execution of renamed paexec via imphash and executable product string
Renamed PowerShell
Detects the execution of a renamed PowerShell often used by attackers or malware
Renamed ProcDump
Detects the execution of a renamed ProcDump executable often used by attackers or malware
Renamed PsExec
Detects the execution of a renamed PsExec often used by attackers or malware
Rundll32 Without Parameters
Detects rundll32 execution without parameters as observed when running Metasploit windows/smb/psexec exploit module
Run PowerShell Script from ADS
Detects PowerShell script execution from Alternate Data Stream (ADS)
Possible Shim Database Persistence via sdbinst.exe
Detects installation of a new shim using sdbinst.exe. A shim can be used to load malicious DLLs into applications.
Service Execution
Detects manual service execution (start) via system utilities
Stop Windows Service
Detects a windows service to be stopped
Shadow Copies Access via Symlink
Shadow Copies storage symbolic link creation using operating systems utilities
Shadow Copies Creation Using Operating Systems Utilities
Shadow Copies creation using operating systems utilities, possible credential access
Shadow Copies Deletion Using Operating Systems Utilities
Shadow Copies deletion using operating systems utilities
Windows Shell Spawning Suspicious Program
Detects a suspicious child process of a Windows shell
Audio Capture via SoundRecorder
Detect attacker collecting audio via SoundRecorder application
Possible SPN Enumeration
Detects Service Principal Name Enumeration used for Kerberoasting
Suspicious AdFind Execution
Detects the execution of a AdFind for Active Directory enumeration
Possible Ransomware or Unauthorized MBR Modifications
Detects, possibly, malicious unauthorized usage of bcdedit.exe
Suspicious Calculator Usage
Detects suspicious use of calc.exe with command line parameters or in a suspicious directory, which is likely caused by some PoC or detection evasion
Possible App Whitelisting Bypass via WinDbg/CDB as a Shellcode Runner
Launch 64-bit shellcode from a debugger script file using cdb.exe.
Certutil Encode
Detects suspicious a certutil command that used to encode files, which is sometimes used for data exfiltration
Suspicious Commandline Escape
Detects suspicious process that use escape characters
Suspicious Code Page Switch
Detects a code page switch in command line or batch scripts to a rare language
Suspicious Compression Tool Parameters
Detects suspicious command line arguments of common data compression tools
Process Dump via Comsvcs DLL
Detects process memory dump via comsvcs.dll and rundll32
Conhost Parent Process Executions
Detects the conhost execution as parent process. Can be used to evaded defense mechanism.
Suspicious Control Panel DLL Load
Detects suspicious Rundll32 execution from control.exe as used by Equation Group and Exploit Kits
Suspicious Copy From or To System32
Detects a suspicious copy command that copies a system program from System32 to another directory on disk – sometimes used to use LOLBINs like certutil or desktopimgdownldr to a different location with a different name
Covenant Launcher Indicators
Detects suspicious command lines used in Covenant luanchers
CrackMapExec Command Execution
Detect various execution methods of the CrackMapExec pentesting framework
CrackMapExec PowerShell Obfuscation
The CrachMapExec pentesting framework implements a PowerShell obfuscation with some static strings detected by this rule.
Suspicious Parent of Csc.exe
Detects a suspicious parent of csc.exe, which could by a sign of payload delivery
Suspicious Csc.exe Source File Folder
Detects a suspicious execution of csc.exe, which uses a source in a suspicious folder (e.g. AppData)
Suspicious Curl Usage on Windows
Detects a suspicious curl process start on Windows and outputs the requested document to a local file
Suspicious Curl File Upload
Detects a suspicious curl process start the adds a file to a web request
Curl Start Combination
Adversaries can use curl to download payloads remotely and execute them. Curl is included by default in Windows 10 build 17063 and later.
Suspicious Desktopimgdownldr Command
Detects a suspicious Microsoft desktopimgdownldr execution with parameters used to download files from the Internet
Devtoolslauncher.exe Executes Specified Binary
The Devtoolslauncher.exe executes other binary
Direct Autorun Keys Modification
Detects direct modification of autostart extensibility point (ASEP) in registry using reg.exe.
Disable Windows Eventlog
Detects command that is used to disable Windows eventlog
Disabled IE Security Features
Detects command lines that indicate unwanted modifications to registry keys that disable important Internet Explorer security features
Raccine Uninstall
Detects commands that indicate a Raccine removal from an end system. Raccine is a free ransomware protection tool.
DIT Snapshot Viewer Use
Detects the use of Ditsnap tool. Seems to be a tool for ransomware groups.
Suspicious Double Extension
Detects suspicious use of an .exe extension after a non-executable file extension like .pdf.exe, a set of spaces or underlines to cloak the executable file in spear phishing campaigns
Application Whitelisting Bypass via Dxcap.exe
Detects execution of of Dxcap.exe
Suspicious Eventlog Clear or Configuration Using Wevtutil
Detects clearing or configuration of eventlogs uwing wevtutil, powershell and wmic. Might be used by ransomwares during the attack (seen by NotPetya and others)
Execution in Non-Executable Folder
Detects a suspicious execution from an uncommon folder
Execution in Webserver Root Folder
Detects a suspicious program execution in a web service root folder (filter out false positives)
Executables Started in Suspicious Folder
Detects process starts of binaries from a suspicious folder
Explorer Root Flag Process Tree Break
Detects a command line process that uses explorer.exe /root, which is similar to cmd.exe /c, only it breaks the process tree and makes its parent a new instance of explorer
Suspicious File Characteristics Due to Missing Fields
Detects Executables in the Downloads folder without FileVersion,Description,Product,Company likely created with py2exe
Findstr Launching .lnk File
Detects usage of findstr to identify and execute a lnk file as seen within the HHS redirect attack
Finger.exe Suspicious Invocation
Detects suspicious aged finger.exe tool execution often used in malware attacks nowadays
Firewall Disabled via Netsh
Detects netsh commands that turns off the Windows firewall
Fsutil Suspicious Invocation
Detects suspicious parameters of fsutil (deleting USN journal, configuring it with small size..). Might be used by ransomwares during the attack (seen by NotPetya and others)
IIS Native-Code Module Command Line Installation
Detects suspicious IIS native-code module installations via command line
Windows Defender Download Activity
Detect the use of Windows Defender to download payloads
Suspicious MsiExec Directory
Detects suspicious msiexec process starts in an uncommon directory
MsiExec Web Install
Detects suspicious msiexec process starts with web addresses as parameter
Malicious Payload Download via Office Binaries
Downloads payload from remote server
Suspicious Netsh DLL Persistence
Detects persitence via netsh helper
Net.exe Execution
Detects execution of Net.exe, whether suspicious or benign.
Invocation of Active Directory Diagnostic Tool (ntdsutil.exe)
Detects execution of ntdsutil.exe, which can be used for various attacks against the NTDS database (NTDS.DIT)
Application Whitelisting Bypass via DLL Loaded by odbcconf.exe
Detects defence evasion attempt via odbcconf.exe execution to load DLL
OpenWith.exe Executes Specified Binary
The OpenWith.exe executes other binary
Suspicious Execution from Outlook
Detects EnableUnsafeClientMailRules used for Script Execution from Outlook
Execution in Outlook Temp Folder
Detects a suspicious program execution in Outlook temp folder
Ping Hex IP
Detects a ping command that uses a hex encoded IP address
Empire PowerShell Launch Parameters
Detects suspicious powershell command line parameters used in Empire
Empire PowerShell UAC Bypass
Detects some Empire PowerShell UAC bypass methods
PowerShell Encoded Character Syntax
Detects suspicious encoded character syntax often used for defense evasion
Suspicious Encoded PowerShell Command Line
Detects suspicious powershell process starts with base64 encoded commands (e.g. Emotet)
Malicious Base64 Encoded PowerShell Keywords in Command Lines
Detects base64 encoded strings used in hidden malicious PowerShell command lines
Suspicious PowerShell Invocation Based on Parent Process
Detects suspicious powershell invocations from interpreters or unusual programs
Suspicious PowerShell Parent Process
Detects a suspicious parents of powershell.exe
Suspicious Program Location Process Starts
Detects programs running in suspicious files system locations
Psexec Accepteula Condition
Detect ed user accept agreement execution in psexec commandline
Psr.exe Capture Screenshots
The psr.exe captures desktop screenshots and saves them on the local machine
PowerShell Script Run in AppData
Detects a suspicious command line execution that invokes PowerShell with reference to an AppData folder
PowerShell DownloadFile
Detects the execution of powershell, a WebClient object creation and the invocation of DownloadFile in a single command line
Rar with Password or Compression Level
Detects the use of rar.exe, on the command line, to create an archive with password protection or with a specific compression level. This is pretty indicative of malicious actions.
Suspicious RASdial Activity
Detects suspicious process related to rasdial.exe
Suspicious Reconnaissance Activity
Detects suspicious command line activity on Windows systems
Regsvr32 Anomaly
Detects various anomalies in relation to regsvr32.exe
Regsvr32 Flags Anomaly
Detects a flag anomaly in which regsvr32.exe uses a /i flag without using a /n flag at the same time
Renamed ZOHO Dctask64
Detects a renamed dctask64.exe used for process injection, command execution, process creation with a signed binary by ZOHO Corporation
Renamed SysInternals Debug View
Detects suspicious renamed SysInternals DebugView execution
Suspicious Rundll32 Activity
Detects suspicious process related to rundll32 based on arguments
Suspicious Call by Ordinal
Detects suspicious calls of DLLs in rundll32.dll exports by ordinal
Suspicious Rundll32 Invoking Inline VBScript
Detects suspicious process related to rundll32 based on command line that invokes inline VBScript as seen being used by UNC2452
Suspicious Process Start Locations
Detects suspicious process run from unusual locations
Scheduled Task Creation
Detects the creation of scheduled tasks in user session
Suspicious Scheduled Task Creation Involving Temp Folder
Detects the creation of scheduled tasks that involves a temporary folder and runs only once
ScreenConnect Remote Access
Detects ScreenConnect program starts that establish a remote access to that system (not meeting, not remote support)
WSF/JSE/JS/VBA/VBE File Execution
Detects suspicious file execution by wscript and cscript
Suspicious Service Binary Directory
Detects a service binary running in a suspicious directory
Suspicious Service Path Modification
Detects service path modification to powershell/cmd
Suspicious Shells Spawn by SQL Server
Detects suspicious shell spawn from MSSQL process, this might be sight of RCE or SQL Injection
ShimCache Flush
Detects actions that clear the local ShimCache and remove forensic evidence
Squirrel Lolbin
Detects Possible Squirrel Packages Manager as Lolbin
Suspicious Svchost Process
Detects a suspicious svchost process start
Suspect Svchost Activity
It is extremely abnormal for svchost.exe to spawn without any CLI arguments and is normally observed when a malicious process spawns the process and injects code into the process memory space.
Sysprep on AppData Folder
Detects suspicious sysprep process start with AppData folder as target (as used by Trojan Syndicasec in Thrip report by Symantec)
Suspicious SYSVOL Domain Group Policy Access
Detects Access to Domain Group Policies stored in SYSVOL
Taskmgr as LOCAL_SYSTEM
Detects the creation of taskmgr.exe process in context of LOCAL_SYSTEM
Taskmgr as Parent
Detects the creation of a process from Windows task manager
Suspicious TSCON Start
Detects a tscon.exe start as LOCAL SYSTEM
Suspicious RDP Redirect Using TSCON
Detects a suspicious RDP session redirect using tscon.exe
Suspicious Userinit Child Process
Detects a suspicious child process of userinit
Suspicious Use of CSharp Interactive Console
Detects the execution of CSharp interactive console by PowerShell
Suspicious VBScript UN2452 Pattern
Detects suspicious inline VBScript keywords as used by UNC2452
Disabled Volume Snapshots
Detects commands that temporarily turn off Volume Snapshots
Whoami Execution
Detects the execution of whoami, which is often used by attackers after exloitation / privilege escalation but rarely used by administrators
Suspicious WMI Execution Using Rundll32
Detects WMI executing rundll32
Wmic Uninstall Security Product
Detects deinstallation of security products using WMIC utility
Suspicious WMI Execution
Detects WMI executing suspicious commands
Windows Update Client LOLBIN
Detects code execution via the Windows Update client (wuauclt)
Suspicious Auditpol Usage
Threat actors can use auditpol binary to change audit policy configuration to impair detection capability. This can be carried out by selectively disabling/removing certain audit policies as well as restoring a custom policy owned by the threat actor.
Sysmon Driver Unload
Detect possible Sysmon driver unload
System File Execution Location Anomaly
Detects a Windows program executable started in a suspicious folder
Tap Installer Execution
Well-known TAP software installation. Possible preparation for data exfiltration using tunneling techniques
Tasks Folder Evasion
The Tasks folder in system32 and syswow64 are globally writable paths. Adversaries can take advantage of this and load or influence any script hosts or ANY .NET Application in Tasks to load and execute a custom assembly into cscript, wscript, regsvr32, mshta, eventvwr
Terminal Service Process Spawn
Detects a process spawned by the terminal service server process (this could be an indicator for an exploitation of CVE-2019-0708)
Domain Trust Discovery
Identifies execution of nltest.exe and dsquery.exe for domain trust discovery. This technique is used by attackers to enumerate Active Directory trusts.
Bypass UAC via CMSTP
Detect child processes of automatically elevated instances of Microsoft Connection Manager Profile Installer (cmstp.exe).
Bypass UAC via Fodhelper.exe
Identifies use of Fodhelper.exe to bypass User Account Control. Adversaries use this technique to execute privileged processes.
Bypass UAC via WSReset.exe
Identifies use of WSReset.exe to bypass User Account Control. Adversaries use this technique to execute privileged processes.
Possible Privilege Escalation via Weak Service Permissions
Detection of sc.exe utility spawning by user with Medium integrity level to change service ImagePath or FailureCommand
Java Running with Remote Debugging
Detects a JAVA process running with remote debugging allowing more than just localhost to connect
Webshell Detection With Command Line Keywords
Detects certain command line parameters often used during reconnaissance activity via web shells
Shells Spawned by Web Servers
Web servers that spawn shell processes could be the result of a successfully placed web shell or an other attack
Run Whoami as SYSTEM
Detects a whoami.exe executed by LOCAL SYSTEM. This may be a sign of a successful local privilege escalation.
Wmiprvse Spawning Process
Detects wmiprvse spawning processes
WMI Backdoor Exchange Transport Agent
Detects a WMi backdoor in Exchange Transport Agents via WMi event filters
WMI Persistence – Script Event Consumer
Detects WMI script event consumers
WMI Spawning Windows PowerShell
Detects WMI spawning PowerShell
Microsoft Workflow Compiler
Detects invocation of Microsoft Workflow Compiler, which may permit the execution of arbitrary unsigned code.
Wsreset UAC Bypass
Detects a method that uses Wsreset.exe tool that can be used to reset the Windows Store to bypass UAC
XSL Script Processing
Extensible Stylesheet Language (XSL) files are commonly used to describe the processing and rendering of data within XML files, rule detects when adversaries abuse this functionality to execute arbitrary files while potentially bypassing application whitelisting defenses
Source
These rules are made by the Sigma Project. This is a collection of rules for several different attack tactics. The rules are created by the Sigma community and translated into the format for the Elastic Security Detection engine.
The translation was made with SIEGMA
| Tested versions | 7.12 |
| ECS compliant |
You must log in to submit a review.