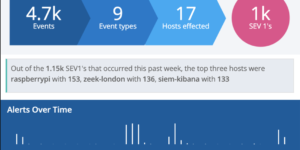
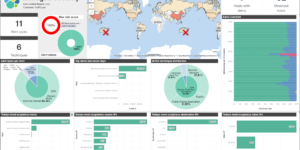
Description
The openSIEM project has developed a couple of Logstash Parsing rules.
The overhead of implementing Logstash parsing and applying Elastic Common Schema (ECS) across audit, security, and system logs can be a large drawback when using Elasticsearch as a SIEM (Security Incident and Event Management). The Cargill SIEM team has spent significant time on developing quality Logstash parsing processors for many well-known log vendors and wants to share this work with the community. In addition to Logstash processors, openSIEM has also included log collection programs for API-based log collection, as well as the setup scripts used to generate pipeline-to-pipeline architecture.
List of sources
api log application oci.object
api log audit aws.cloudtrail
api log audit aws.ghe
api log audit oci.audit
api log audit okta
api log audit syncplicity.adm report
api log audit syncplicity.usr report
api log network aws.vpcflow
api log network oci.vcn
api log security aws.guardduty
api log security azure.atp
api log security azure.graph api
api log security azure.graph identity protection api
api log security azure.mcas alerts
api log security azure.o365 dlp
api log security jamf.protect
api log security mcafee.mcp v5
api log security misp.metrics
api log security oci.cloudguard
api log security proofpoint.pod email gateway
api log security proofpoint.siem api clicks
api log security proofpoint.siem api message
api log security scorecard.events
atlassian jira
atlassian jira audit
db log audit citrix.session
event hub log audit azure.event hub audit
event hub log audit azure.event hub operational
event hub log audit azure.event hub signin
event hub log audit o365.dlp
event hub log audit o365.msg.trkg eventhub
event hub log security azure.event hub
event hub log security azure.event hub atp
flat file log audit ansible
flat file log audit apache.access
flat file log audit apache.error
flat file log audit exchange.2016.msg.trkg
flat file log audit iis
flat file log audit microsoft.iis.w3c
flat file log audit mwg.proxy
flat file log audit pingfederate
flat file log audit riverbed.amauth
flat file log audit riverbed.audit
flat file log audit riverbed.opnetreport
flat file log audit riverbed.scportal
flat file log audit riverbed.stdout
flat file log audit riverbed.vnes analytics
flat file log security windows.exported security events
ftp gzip log audit infoblox dns
log audit apache
log security preempt monthly
logstash virtustream linux forwarder
logstash virtustream windows forwarder
push api list inventory forescout
syslog audit linux rsyslog
syslog list inventory tanium
syslog log audit a10.proxy
syslog log audit accellion.sft
syslog log audit checkpoint.fw
syslog log audit checkpoint.operations
syslog log audit cisco.aci
syslog log audit cisco.dna
syslog log audit cisco.mso
syslog log audit cisco.prime
syslog log audit cisco.router
syslog log audit cisco.switch
syslog log audit cisco.wireless.ap
syslog log audit cisco.wireless.bridge
syslog log audit cisco.wireless.control.system
syslog log audit citrix.netscaler
syslog log audit f5.big.ip.gtm.dns
syslog log audit f5.big.ip.ltm
syslog log audit infoblox
syslog log audit lieberman.random.pass.mgr
syslog log audit linux.host
syslog log audit linux.redhat
syslog log audit meraki.router
syslog log audit mpki.cmpv2
syslog log audit riverbed.netim weekly
syslog log audit rsa.auth
syslog log audit spectracom.ntp
syslog log audit tenable.nessus scanner
syslog log audit tenable.security center
syslog log audit ubiquiti.controller session logs
syslog log audit ubiquiti.wireless bridge
syslog log security a10.waf
syslog log security bomgar
syslog log security cisco.apic
syslog log security cisco.ise
syslog log security cisco.meraki.fw
syslog log security cisco.meraki.wap
syslog log security cisco.satellite
syslog log security cisco.stealthwatch
syslog log security cisco.waas
syslog log security forescout.counteract.nac
syslog log security guardium.db
syslog log security hp.network.node.mgr
syslog log security juniper.fw
syslog log security juniper pulse.ssl.vpn
syslog log security layer7.securespan.soa.gw
syslog log security mcafee.atd
syslog log security mcafee.mwg
syslog log security mcafee.net.security.mgr
syslog log security microsoft.ata
syslog log security palo.alto.fw
syslog log security sap.onapsis
syslog log security sdwan.app
syslog log security sdwan.os ubuntu
syslog log security symantec.dlp
syslog log security symantec.endpoint
syslog log security tanium
syslog log security tufin
syslog log source unidentified
test log security proofpoint.forensics api monthly
wef log audit windows.events
Source
Originally found here: https://github.com/Cargill/OpenSIEM-Logstash-Parsing
| Tested versions | 7.15 |
| ECS compliant | Yes |
You must log in to submit a review.