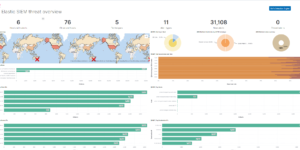
Description
This are ACSC Advisory IOCs detection rules for Elastic SIEM.
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques and procedures used against multiple Australian businesses in a recent campaign by a state based actor.
SIEM rules were created using the list of IOCs published by the ACSC to detect and alert on a potential attack.
IOCs often change rapidly during campaigns and should not solely be relied upon for detections. However, it can be useful to maintain a list of IOCs in case other lines of defence are bypassed by the adversary.
Note that the SIEM rules currently run every 60 minutes, looking back at events from the last 60 minutes. The rules currently do not run actions for every execution. If you need to act on detections, it would be a good idea to set the frequency to Hourly rather than on each rule execution, to reduce the amount of noise created.
Here is a full blog post on the campaign and Elastic Security.
Source
Originally found here: https://github.com/elastic/examples/tree/master/Security%20Analytics/ACSC2020-008_IOCs
| Tested versions | 7.13 |
| ECS compliant | Yes |
You must log in to submit a review.