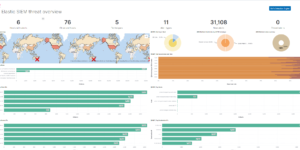
Description
This is a collection of SIEM detection rules in Elastic Security for Windows based on the Sigma project. This rule collection checks about sysmon events to find common threats. Sysmon is an enhanced event collection for Windows systems and offers better visibility into what is happening on windows systems.
SIEM detection rules
CMSTP Execution Process Access
Detects various indicators of Microsoft Connection Manager Profile Installer execution
Credentials Dumping Tools Accessing LSASS Memory
Detects process access LSASS memory which is typical for credentials dumping tools
Suspect Svchost Memory Asccess
Detects suspect access to svchost process memory such as that used by Invoke-Phantom to kill the winRM windows event logging service.
Credential Dumping by LaZagne
Detects LSASS process access by LaZagne for credential dumping.
LSASS Memory Dump
Detects process LSASS memory dump using procdump or taskmgr based on the CallTrace pointing to dbghelp.dll or dbgcore.dll for win10
Malware Shellcode in Verclsid Target Process
Detects a process access to verclsid.exe that injects shellcode from a Microsoft Office application / VBA macro
Mimikatz through Windows Remote Management
Detects usage of mimikatz through WinRM protocol by monitoring access to lsass process by wsmprovhost.exe.
Dllhost Internet Connection
Detects Dllhost that communicates with public IP addresses
Suspicious Typical Malware Back Connect Ports
Detects programs that connect to typical malware back connect ports based on statistical analysis from two different sandbox system databases
Notepad Making Network Connection
Detects suspicious network connection by Notepad
RDP Over Reverse SSH Tunnel
Detects svchost hosting RDP termsvcs communicating with the loopback address and on TCP port 3389
Remote PowerShell Session
Detects remote PowerShell connections by monitoring network outbount connections to ports 5985 or 5986 from not network service account
Rundll32 Internet Connection
Detects a rundll32 that communicates with public IP addresses
Suspicious Outbound Kerberos Connection
Detects suspicious outbound network activity via kerberos default port indicating possible lateral movement or first stage PrivEsc via delegation.
Suspicious Program Location with Network Connections
Detects programs with network connections running in suspicious files system locations
Suspicious Outbound RDP Connections
Detects Non-Standard Tools Connecting to TCP port 3389 indicating possible lateral movement
Microsoft Binary Github Communication
Detects an executable in the Windows folder accessing github.com
Microsoft Binary Suspicious Communication Endpoint
Detects an executable in the Windows folder accessing suspicious domains
Abusing Azure Browser SSO
Detects abusing Azure Browser SSO by requesting OAuth 2.0 refresh tokens for an Azure-AD-authenticated Windows user (i.e. the machine is joined to Azure AD and a user logs in with their Azure AD account) wanting to perform SSO authentication in the browser. An attacker can use this to authenticate to Azure AD in a browser as that user.
PowerShell Execution
Detects execution of PowerShell
Fax Service DLL Search Order Hijack
The Fax service attempts to load ualapi.dll, which is non-existent. An attacker can then (side)load their own malicious DLL using this service.
Possible Process Hollowing Image Loading
Detects Loading of samlib.dll, WinSCard.dll from untypical process e.g. through process hollowing by Mimikatz
dotNET DLL Loaded Via Office Applications
Detects any assembly DLL being loaded by an Office Product
CLR DLL Loaded Via Office Applications
Detects CLR DLL being loaded by an Office Product
GAC DLL Loaded Via Office Applications
Detects any GAC DLL being loaded by an Office Product
Active Directory Parsing DLL Loaded Via Office Applications
Detects DSParse DLL being loaded by an Office Product
Active Directory Kerberos DLL Loaded Via Office Applications
Detects Kerberos DLL being loaded by an Office Product
Unsigned Image Loaded Into LSASS Process
Loading unsigned image (DLL, EXE) into LSASS process
WMI Modules Loaded
Detects non wmiprvse loading WMI modules
WMI Persistence – Command Line Event Consumer
Detects WMI command line event consumers
File Created with System Process Name
Detects the creation of a executable with a system process name in a suspicious folder
Cred Dump Tools Dropped Files
Files with well-known filenames (parts of credential dump software or files produced by them) creation
Detection of SafetyKatz
Detects possible SafetyKatz Behaviour
LSASS Memory Dump File Creation
LSASS memory dump creation using operating systems utilities. Procdump will use process name in output file if no name is specified
Microsoft Office Add-In Loading
Detects add-ins that load when Microsoft Word or Excel starts (.wll/.xll are simply .dll fit for Word or Excel).
Malicious PowerShell Commandlet Names
Detects the creation of known powershell scripts for exploitation
QuarksPwDump Dump File
Detects a dump file written by QuarksPwDump password dumper
RedMimicry Winnti Playbook Dropped File
Detects actions caused by the RedMimicry Winnti playbook
Suspicious ADSI-Cache Usage By Unknown Tool
Detects the usage of ADSI (LDAP) operations by tools. This may also detect tools like LDAPFragger.
Windows Webshell Creation
Possible webshell file creation on a static web site
WMI Persistence – Script Event Consumer File Write
Detects file writes of WMI script event consumer
Suspicious Desktopimgdownldr Target File
Detects a suspicious Microsoft desktopimgdownldr file creation that stores a file to a suspicious location or contains a file with a suspicious extension
Suspicious Driver Load from Temp
Detects a driver load from a temporary directory
Source
These rules are made by the Sigma Project. This is a collection of rules for several different attack tactics. The rules are created by the Sigma community and translated into the format for the Elastic Security Detection engine.
The translation was made with SIEGMA
| Tested versions | 7.12 |
| ECS compliant |
You must log in to submit a review.