Description
This is a collection of Elastic Security Detection rules for Zeek (aka Bro), based on the Filebeat Zeek module. Security Detection rules are used to detect suspicous behavior within your data. Every rule is checking for specific problematic behavior.
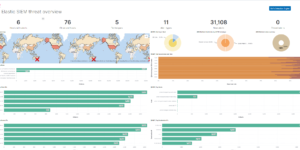
SIEM detection rules
The following SIEM detection rules are included.
MITRE BZAR Indicators for Execution:
Windows DCE-RPC functions which indicate an execution techniques on the remote system. All credit for the Zeek mapping of the suspicious endpoint/operation field goes to MITRE.
MITRE BZAR Indicators for Persistence:
Windows DCE-RPC functions which indicate a persistence techniques on the remote system. All credit for the Zeek mapping of the suspicious endpoint/operation field goes to MITRE.
Executable from Webdav:
Detects executable access via webdav6. Can be seen in APT 29 such as from the emulated APT 29 hackathon https://github.com/OTRF/detection-hackathon-apt29/ .
Publicly Accessible RDP Service:
Detects connections from routable IPs to an RDP listener – which is indicative of a publicly-accessible RDP service.
Remote Task Creation via ATSVC Named Pipe – Zeek:
Detects remote task creation via at.exe or API interacting with ATSVC named pipe.
Possible Impacket SecretDump Remote Activity – Zeek:
Detect AD credential dumping using impacket secretdump HKTL. Based on the SIGMA rules/windows/builtin/win_impacket_secretdump.yml
Source
These rules are made by the Sigma Project. This is a collection of rules for several different attack tactics. The rules are created by the Sigma community and translated into the format for the Elastic Security Detection engine.
The translation was made with SIEGMA
| Tested versions | 7.5 |
| ECS compliant |
You must log in to submit a review.