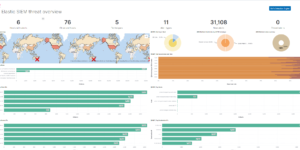
Description
This is a collection of Elastic Security SIEM detection rules for AWS cloudtrail based on Sigma rules. The detection rules for Elastic Security offer a great possibility to observe data for threats. This collection analysis AWS data that is collection with the AWS integration of the Elastic Agent or Filebeat.
SIEM Detection rules
These Sigma AWS Cloudtrail Detection rules are included in this collection:
AWS CloudTrail Important Change
Detects disabling, deleting and updating of a Trail
AWS Config Disabling Channel/Recorder
Detects AWS Config Service disabling.
AWS EC2 Startup Shell Script Change
Detects changes to the EC2 instance startup script. The shell script will be executed as root/SYSTEM every time the specific instances are booted up.
AWS EC2 VM Export Failure
An attempt to export an AWS EC2 instance has been detected. A VM Export might indicate an attempt to extract information from an instance.
AWS GuardDuty Important Change
Detects updates of the GuardDuty list of trusted IPs, perhaps to disable security alerts against malicious IPs.
AWS IAM Backdoor Users Keys
Detects AWS API key creation for a user by another user. Backdoored users can be used to obtain persistence in the AWS environment. Also with this alert, you can detect a flow of AWS keys in your org.
AWS RDS Master Password Change
Detects the change of database master password. It may be a part of data exfiltration.
Restore Public AWS RDS Instance
Detects the recovery of a new public database instance from a snapshot. It may be a part of data exfiltration.
AWS Root Credentials
Detects AWS root account usage
AWS User Login Profile Was Modified
An attacker with the iam:UpdateLoginProfile permission on other users can change the password used to login to the AWS console on any user that already has a login profile setup. With this alert, it is used to detect anyone is changing password on behalf of other users.
Source
These rules are made by the Sigma Project. This is a collection of rules for several different attack tactics. The rules are created by the Sigma community and translated into the format for the Elastic Security Detection engine.
The translation was made with SIEGMA
| Tested versions | 7.1, 7.10 |
| ECS compliant |
You must log in to submit a review.