Description
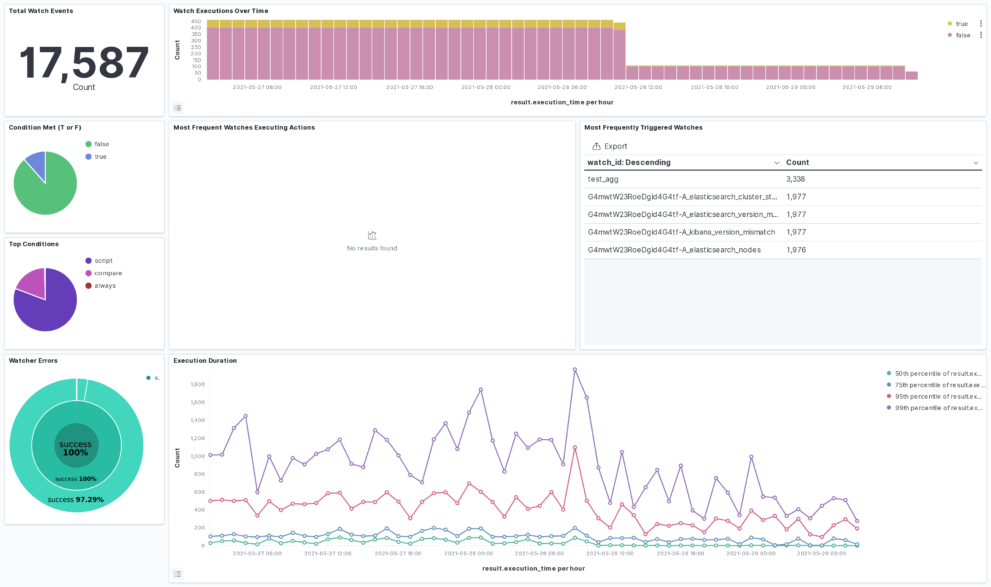
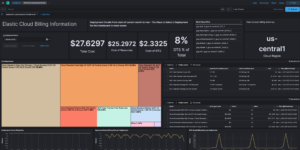
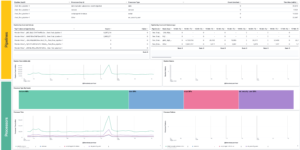
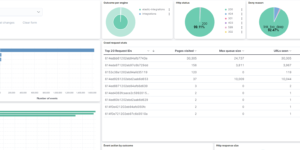
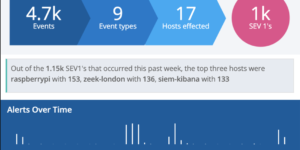
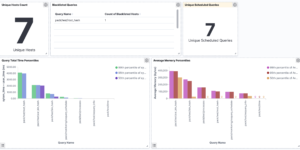
The Watcher History Dashboard shows the history of all the watcher jobs that are configured in your Elasticsearch deployment. This works by taking data from the system watcher history index that is created automatically when you are using watchers.
This is an Kibana example dashboard that can be easily extended based on your own needs. Also have a look into our Watcher job library if you need more information regardings watchers and what you can do with it.
| Tested versions | 7.12 |
| ECS compliant |
You must log in to submit a review.